Simon Fletcher
Simon Fletcher
Cybersecurity affects us all. Whether you’re a teenager Snap Chatting friends, a barrister working remotely, owner of a large corporate or a grandmother keeping in touch with far flung relatives, Cybersecurity is an issue that needs to be brought to the fore…especially with the current challenges in the world today.
However, that doesn’t mean that we are all experts in how we keep ourselves safe in the Cyberworld. Speak to many teenagers and they’re knowledge is drawn from Tik Tok, adults from chat rooms, bogus click bait articles, the list goes on. We all know passwords hold the key to our online data but how do we know whether we’re treating them with the importance they require and at a level that keeps us safe?
These are three statements of security advice and reasons they were believed that I have genuinely heard people say. Only one is correct, which one? Read on and find out….
- When sending passwords to other people/users it should be sent via text message (SMS).
Emails are an insecure method of sending sensitive information. Therefore, if you are sending a password you should send it via text message. For example, if you email a file with highly confidential information you should encrypt that file and send the password via text message.
- A passphrase of seven random words is virtually uncrackable.
Even if a hacker knows you’ve created a passphrase of seven common words, and they know the list of words you selected them from. Your passphrase in virtually uncrackable. This is because there are so many combinations of words, that even the NSA – who can attempt 1 trillion passwords combination per second – would take millions of years to crack it.
- You should not use password managers to store all your passwords as they often have vulnerabilities in them.
Password managers, such as LastPass, 1Password and many more, are often toted as a secure way to keep your passwords. However, these password managers are just software, and like all software they have vulnerabilities in them. If a hacker can exploit these vulnerabilities, then they can access all your passwords and it is game over. As the saying goes, don’t keep all your eggs in one basket.
If you’ve not watched the video and don’t know the answer, then feel free to have a guess yourself now.

The Answer…drum roll…
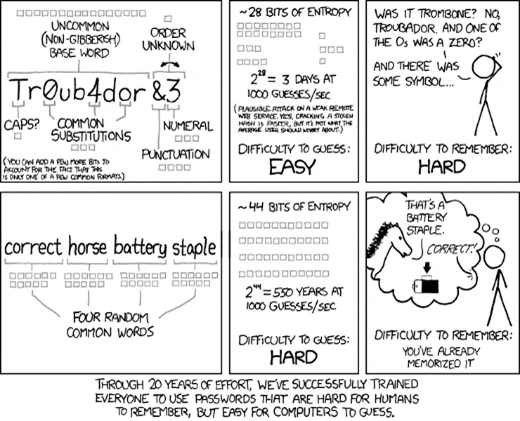
The correct answer was number 2. An XKCD comic – often referred to as “Correct Horse Battery Staple” – proposed that selecting four random common English words is more secure than choosing an uncommon word and changing some characters for numbers and symbols.
The XKCD comic was probably based on a paper by Arnold Reinhold who proposed using a series of dice throws to select a number of words from a list of 7,776. Reinhold called this method “Diceware”.
The Intercept’s Micah Lee explains they use Diceware to generate a seven-word passphrase for anonymous sources to uploading document onto their systems. Their sources need to protect themselves from nation state actors like the NSA.
There are 1.7 Octillion combinations of a seven-word Diceware passphrase. That’s 1.727 or if you really want to see that as an actual number, it’s 1,719,070,799,748,422,800,000,000,000.
So even the NSA – with its trillion-guess-per-second cracking – would take 27 million years.
Of course, as another XKCD comic once pointed out; people are usually the weakest link. Why would you spend millions on a supercomputer to crack strong password when you can beat it out of them?
So statement 1 is false? I had no idea…
I have heard many people tell me that passwords must be sent via text message “For security”. Unfortunately, these people are often repeating doctrine, without understanding the reason behind it. Only a couple of months back, I had someone ask me for my phone number over chat so they could text me a password. Oh boy, there is a lot to unpack there.
First, the level of security measures you take depend on who you’re keeping it a secret from and who you trust. Let’s assume for our day-to-day needs that nation states are not interested in your excel file of employee salaries and that we trust the administrators of our systems. If your daily activities include sending plans for a secret nuclear weapons program, then trust no-one. For the rest of us we can make some assumptions about trust.
There are probably two scenarios where you will want to send someone a password:
So that the recipient can open an encrypted file.
We could simply email it based on our assumptions of trust. However, that depends. If you’ve just emailed them the file, the risk is that if their email account is compromised in the future, and the hacker has access to both the password and the encrypted file. Therefore, it’s a good idea to send the password via a different channel to the encrypted file. Which is why we often see passwords being sent via text message. So long as it’s a different channel, for example sending an encrypted file on a USB by post and sending the password by carrier pigeon has the same effect.
So that someone can access as new computer system.
Again we could simply email it to them. However, again if their email account is compromised in the future then the hacker has access to all those systems too. That is unless you’ve changed your password on the target system. Therefore, many systems will force users to change their password on first login and expire the password after a period if the user doesn’t login at all.
If I go back to my friend who asked me for my telephone number over chat so he could send me a password, in that instance the password was for a new system which forced the user to select a new password on login. At the time I asked him to just email me the password. But he insisted that he had to send it via SMS as that is what the process said. I then asked him to simply send it over the chat we were conversing on, but again be refused. I then asked why if he didn’t trust this chat medium, why was he asking for my phone number. If I wasn’t who he thought I was, I’d give him a number I had access to anyway. Again, he refused and still refused even after I’d politely explained all the flaws in what he was asking. Eventually, I resigned, gave him my phone number and chalked it up to some people just want to follow rules and are not interested in understanding the reasoning.

So can I use Password Managers?
Password managers (PM) are vulnerable to security vulnerabilities just like all software. When a vulnerability is discovered and published there is often a chorus of people saying that you should not use that particular PM or even in some cases that you shouldn’t use any PM.
However, the alternative to using password managers is too horrendous to consider. We have so many passwords to remember these days that even if we do pick a secure password, like the Diceware method. We naturally reuse that password for multiple systems. This where hackers would use something called “Credential Stuffing”. Hackers use information from password breaches to attempt to gain access to other systems with the credentials from the breach.
I’ll hold my hand up, I once got caught out reusing a password. I had several “levels” of passwords. The lowest level was the password I used for all the systems of low value and the highest level I only used for things like my online banking. Then LinkedIn was breached, and my low-level password was in the public domain. That’s when I started using a PM. Unfortunately, before I could update all my account my Netflix account got breached and I was locked out. Yes, that’s right I used my low-level password for Netflix… DOH! Fortunately, there was no lasting damage, I reported it to Netflix and they soon gave me access to my account, but the hacker had removed all my viewing history, which meant I lost where I was in various series I’d been watching. So, that time I was lucky, and it was just an inconvenience. But now all my accounts have unique passwords, all generated by my PM.
Yes, there are occasional vulnerabilities discovered in PMs. But generally, these companies are quick to fix them and issue security updates. You are putting all you egg in one basket… but it’s a pretty secure basket.
Wrap-up
So as you can see, there are a lot of myths and untruths about cybersecurity out there, it advances so quickly that a truth can become false in no time at all. Questioning what you believe to be correct can be the challenge. Contact our expert team at Cyberfort for any questions you may have to protect your company and employees. Keep ahead of cybercrime and keep safe.
Phishing for the truth
Watch the full video here to see other truth’s and lies that our cybersecurity experts discussed

Recent Comments