
![CHECK-Penetration-Testing (003)[91] CHECK penetration testing assurance logo](https://cyberfortgroup.com/wp-content/uploads/2020/03/CHECK-Penetration-Testing-00391.png)


Article 32 of GDPR states that data controllers and processors should implement appropriate “technical and organisational measures to ensure a level of security appropriate to the risk” and that there should be a “process for regularly testing, assessing and evaluating the effectiveness” of these measures to ensure the security of processing.
Regular penetration testing helps to satisfy this requirement.

The Benefits of Penetration Testing
The General Data Protection Regulation (GDPR) came into force in May 2018, and cyber security is at the heart of it, with significant fines and penalties being issued for non-compliance.
The need for regular robust security testing is outlined in the regulation and is therefore essential to compliance.
Failing to regularly test your systems will act as a clear sign to regulators that security is not being taken seriously, and could lead to devastating consequences for your business.
It is advised that you perform penetration tests annually, or when any significant changes are made to your IT estate.
As a minimum, both an external and internal network infrastructure test should be carried out in order to satisfy regulators.
If your organisation has an application that was specifically coded for you, either internally or externally, application penetration testing will also verify that the developers have implemented the proper access controls.
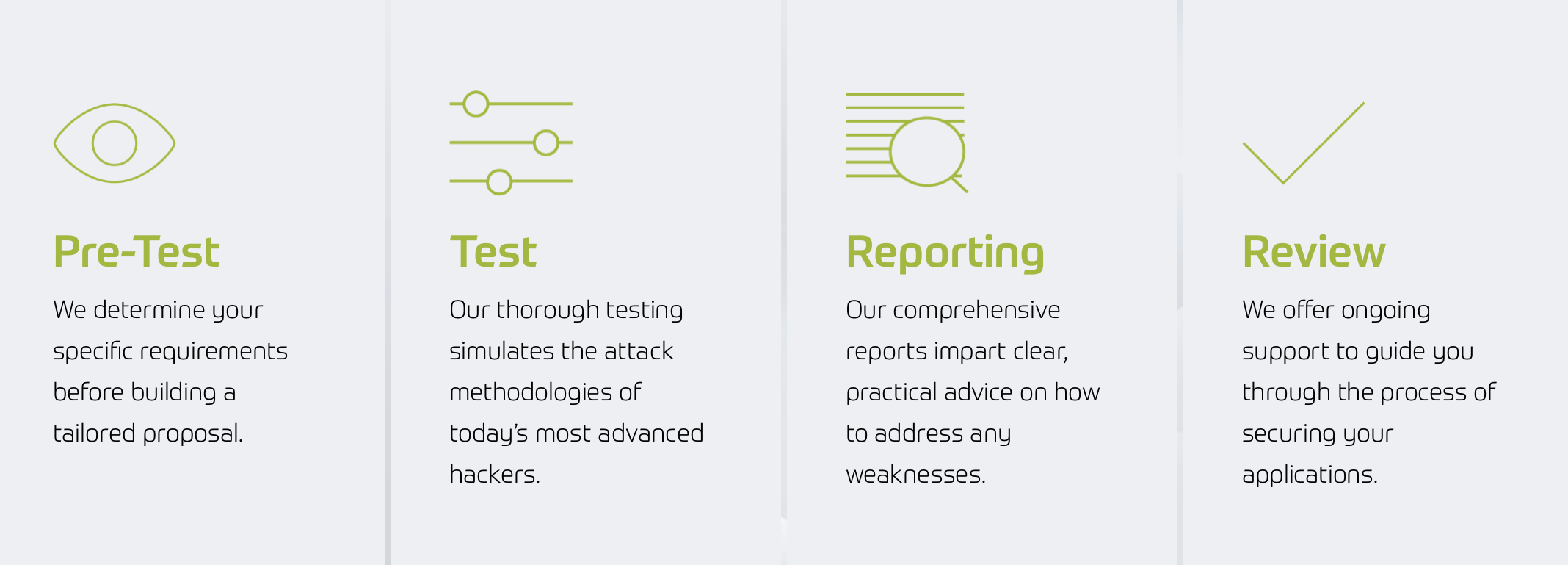
What Happens During a Penetration Test?
During our penetration tests, our expert team emulate the attack methodologies and advanced techniques used by cyber criminals and malicious insiders, verifying that all the relevant security controls are in place, or highlighting any weaknesses within the corporate system.
At Arcturus, every customer is provided with a detailed report which acts as an action plan to help you remediate any vulnerabilities. We also carry out a full debrief and work with you to improve your cyber security standing and address any issues before they impact your business.
How We Work
Other Services


