
![CHECK-Penetration-Testing (003)[91] CHECK penetration testing assurance logo](https://cyberfortgroup.com/wp-content/uploads/2020/03/CHECK-Penetration-Testing-00391.png)


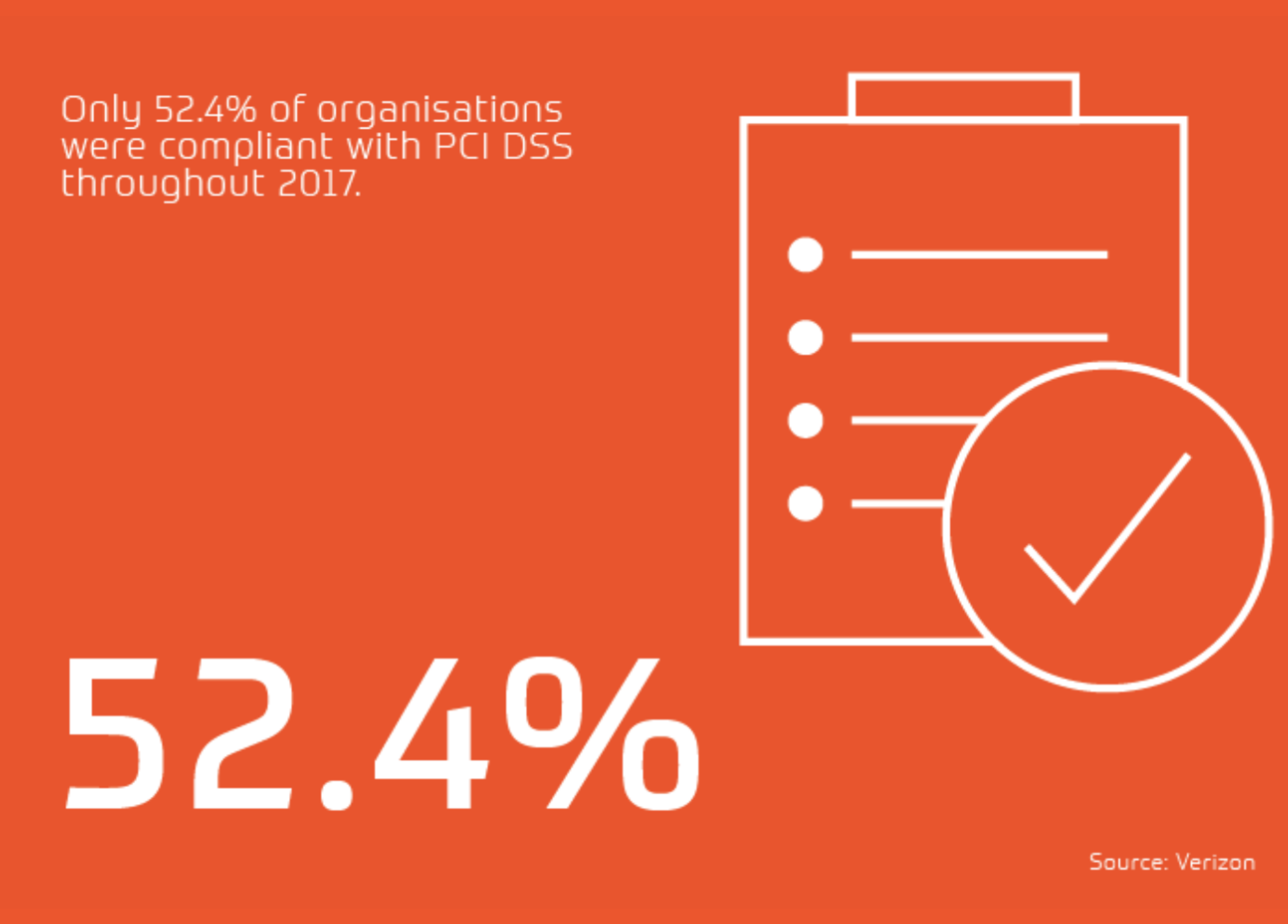
If your organisation stores or processes card details, you need to comply with the worldwide Payment Card Industry Data Security Standard (PCI DSS) in order to safeguard information.
Regular security testing is necessary – it’s clearly outlined in ‘Requirement 11: Regularly test security systems and processes’, which states the need to ‘implement a methodology for penetration testing’.
It can also be difficult to get to grips with the detail behind the many requirements of this payment standard. This is where our expert team can help you satisfy regulators.

Penetration Testing is a requirement
PCI DSS centres around protecting cardholder data, setting out tight controls surrounding the storage, transmission and processing of financial information handled by businesses.
This information is also considered Personally Identifiable Information (PII) and is therefore covered by GDPR, meaning that the fines following a breach are now considerably larger than they previously were.
You must provide evidence of both network and application penetration tests to achieve compliance with this standard. If not, you risk hefty financial penalties.
Annual external and internal network infrastructure tests, as well as application penetration tests must be carried out on all systems, alongside additional tests following any changes.
These tests lay the foundations for maintaining strict security measures and developing a robust strategy to safeguard payment data and become compliant with PCI DSS.
11.3 Implement a Methodology for Penetration Testing
- Based on industry-accepted pen testing approaches
- Includes coverage for the CDE perimeter and critical systems
- Includes testing of internal and external networks and validation of segmentation and scope-reduction controls
- Defines application-layer penetration tests and network-layer penetration tests including components that support network functions and operating systems
- Includes a review of threats and vulnerabilities experienced in the last 12 months
- Specifies retention of pen testing results and remediation activities
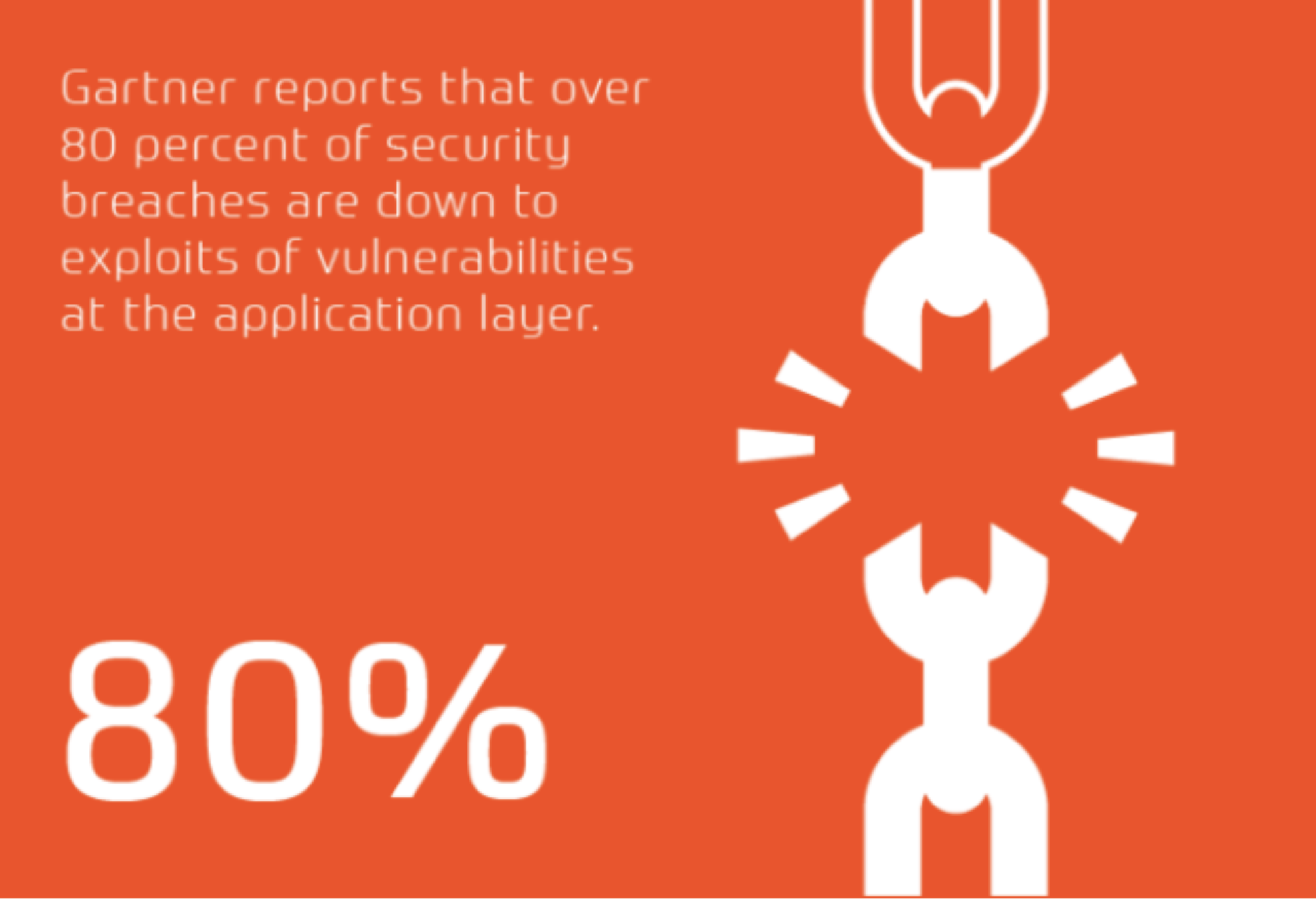
Factors that Affect the Security of Your Product
- Pressure on development teams to build better, more feature-rich software to ever-tightening deadlines means that security is often an afterthought.
- Increased reliance on third-party software components and offshore development houses can increase the attack surface and result in unforeseen back doors in your application.
- Traditional monolithic applications are being replaced by bespoke or niche high-volume micro development projects which are more difficult to secure, manage and maintain.
- Agile and rapid development techniques lead to compressed release and test schedules which require innovative solutions to incorporate security testing without introducing unacceptable delays & costs.
INFOGRAPHIC TO BE INSERTED
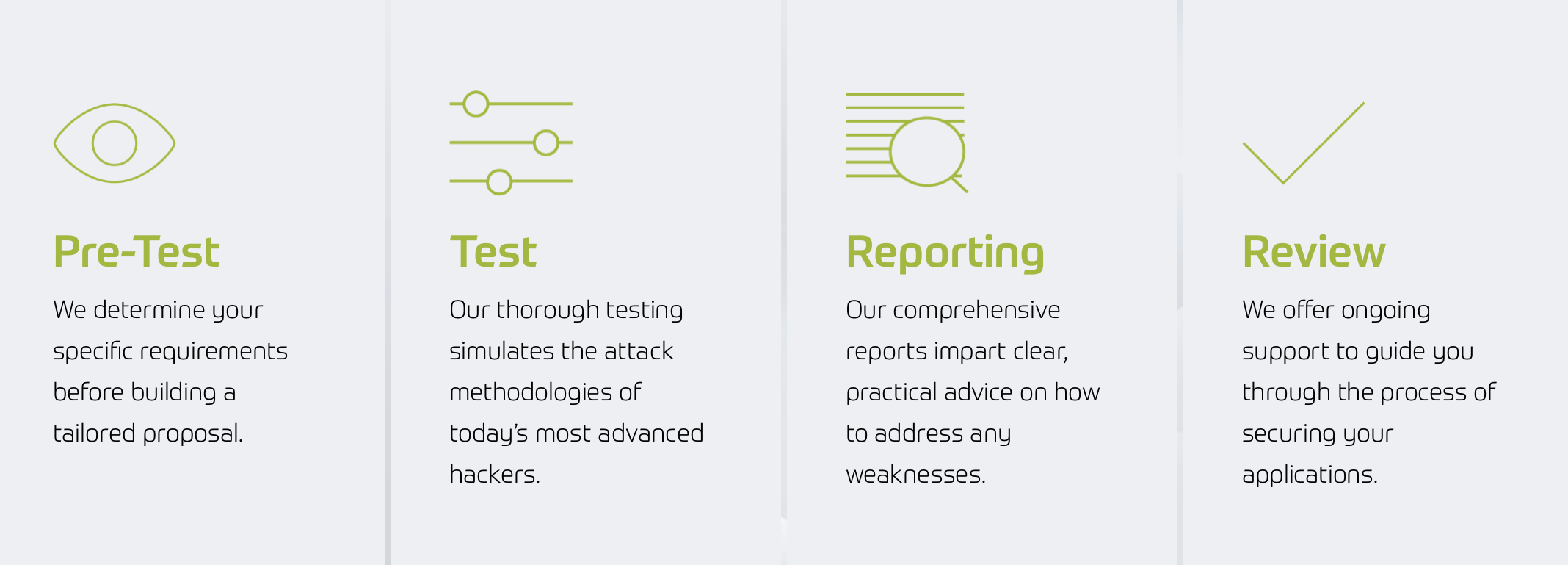
How We Work

Robust Security Makes Compliance Simple
Implementing good security practices can mean that compliance with PCI DSS is a given.
Showing that you have robust security strategies in place, and that they are continuously being tested and maintained, will help you safeguard sensitive payment data and evidence that you are adhering to the requirements of PCI DSS.
Other Services


